Windows Firewall Playground
Prerequisites¶
- VirtualBox or VMware Workstation Pro Installed.
- Virtual Machine
[project-x-win-client].
Network Topology¶
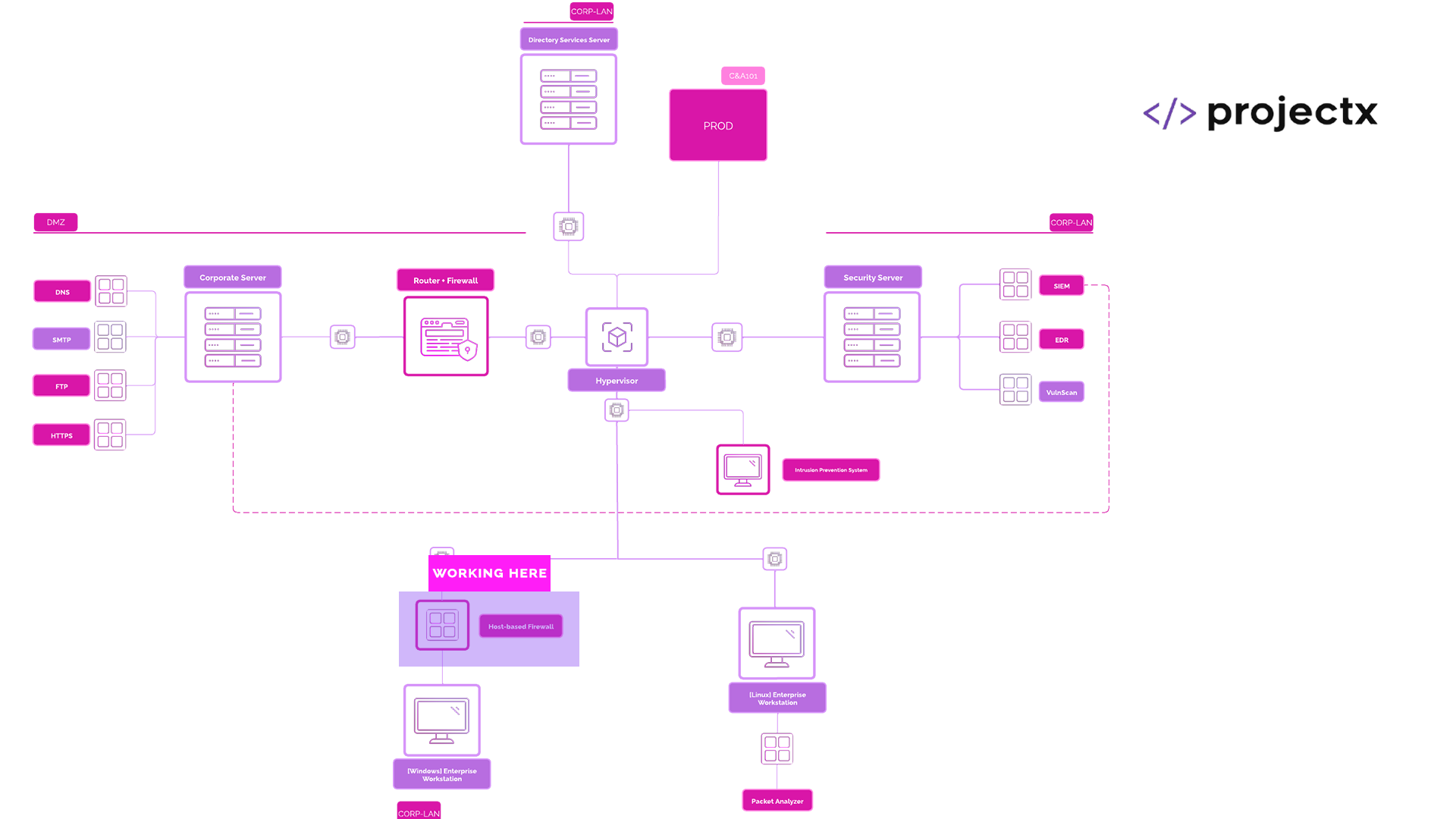
Firewall Overview¶
A firewall is a network security system that monitors and controls incoming and outgoing traffic based on predefined rules. It acts as a barrier between trusted and untrusted networks, helping prevent unauthorized access.
Windows Firewall¶
Windows Firewall is a host-based firewall built into the Windows operating system. It allows users to configure rules for both inbound and outbound traffic, offering basic protection against unsolicited connections and some types of malware communication.
Security Implications¶
A properly configured firewall helps block malicious traffic, reduce the attack surface, and enforce access control policies. Misconfigured firewalls can allow unauthorized access or block legitimate traffic, leading to security gaps or service disruptions.
INBOUND & OUTBOUND¶
Inbound traffic refers to data packets originating from external sources trying to reach local devices or services. Outbound traffic is data sent from internal devices to external destinations. Managing both is critical to prevent external attacks and control internal data exfiltration.
This is going to be a very easy exercise. Most of the time, we do not even interface with the Windows Firewall.
What we are attempting to do here is to start getting you to think about INBOUND and OUTBOUND Firewall rules. What works, what doesn't, and why.
Open Windows Defender Firewall¶
Search "Windows Defender Firewall" in the search bar.
Choose "Advanced Settings". Type in the Administrator username and password.
We now see Windows Firewall.
Windows Firewall provides a solid basis for firewall basics, blocking and denying based on inbound or outbound network requests.
Create INBOUND Rule¶
We are going to block port 443 (HTTP) as an inbound rule. Before we do this, guess...
Will we be able to navigate to any website once this rule is implemented?
Right-click on "Inbound Rules" ➔ "New Rule...".
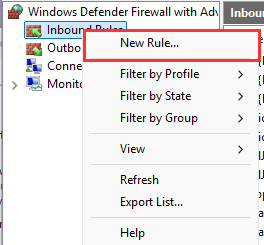
Here we can define our rule type, let's keep it simple, choose "Port".
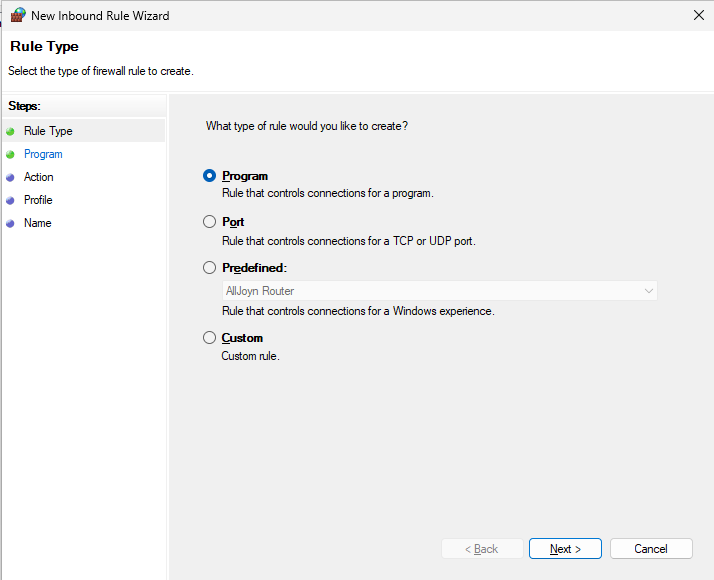
Keep "TCP", type 443.
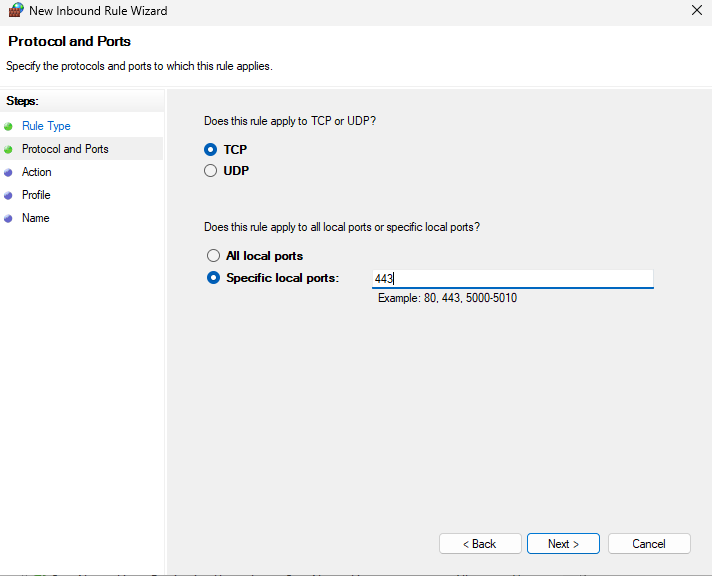
Select "Block the connection".
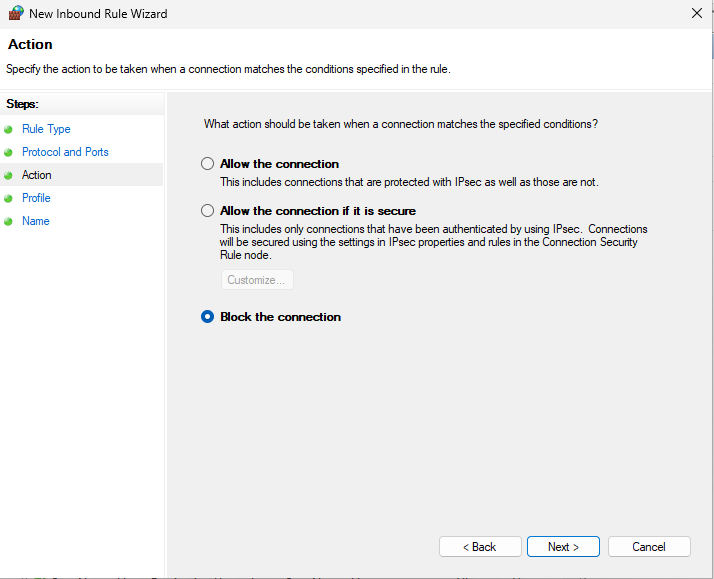
Name the rule "Block 443" ➔ Finish.
Navigate to https://youtube.com.
Does this work?
Nope. Think about why.
Create OUTBOUND Rule¶
Disable the INBOUND rule by Right-clicking "Block 443" ➔ "Disable".
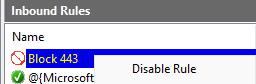
Recreate the same exact rule, except under OUTBOUND.
Navigate to https//youtube.com.
Does it get blocked?
Yep.
What's happening?¶
When the network packet hits the network interface, it will go through its OUTBOUND interface. The Windows Firewall will intercept the request and compare its destination port (443) to its OUTBOUND table, if a match is met, then it will handle it according to its rule definition. In this case, we are blocking any OUTBOUND requests.
When enabling the INBOUND rule, it works because when hitting the OUTBOUND network interface, there is no rules matching port 443, meaning it will pass the traffic along.
Wouldn't the packets be blocked when routing from https://youtube.com back to our computer?
The Windows Firewall is called a "Stateful Firewall". This means that when the network packets hits network interface, reply traffic will automatically be let back in if the rule allows it.
A "Stateless Firewall" does the opposite. Firewall rules must be created for both INBOUND and OUTBOUND network traffic. If the Windows Firewall was stateless, our reply traffic from YouTube to our computer (really the router) will be rejected.
Stateless Firewalls are mostly a technology of the past. Their simplicity and efficiency make them useful in certain scenarios, but they lack a handful of key features to monitor and block network traffic at scale.
Although this exercise accomplishes almost nothing, this showcases the basic primitives behind INBOUND and OUTBOUND interfaces and stateful or stateless firewall types.
Each interface and type of firewall comes with its sets of implications.
We will be doing more of a "deep dive" when we deploy our pfSense Firewall.