Overview
Project Overview¶
Welcome to Networks & Attacks 101.
This course, referred to as a "Core Section", is all about learning the foundations of networking, while working on hands-on scenarios to learn about network attack techniques and defenses deployed to protect enterprise networks.
Built off of Enterprise 101's topology and infrastructure, this Core Section is bundled with the basics, while attempting to explain the why.
The Overview Guide is here to help outline pertinent information related to this Core Section. It is assumed all infrastructure, accounts, and VMs have been deployed and configured in Enterprise 101.
Network Topologies¶
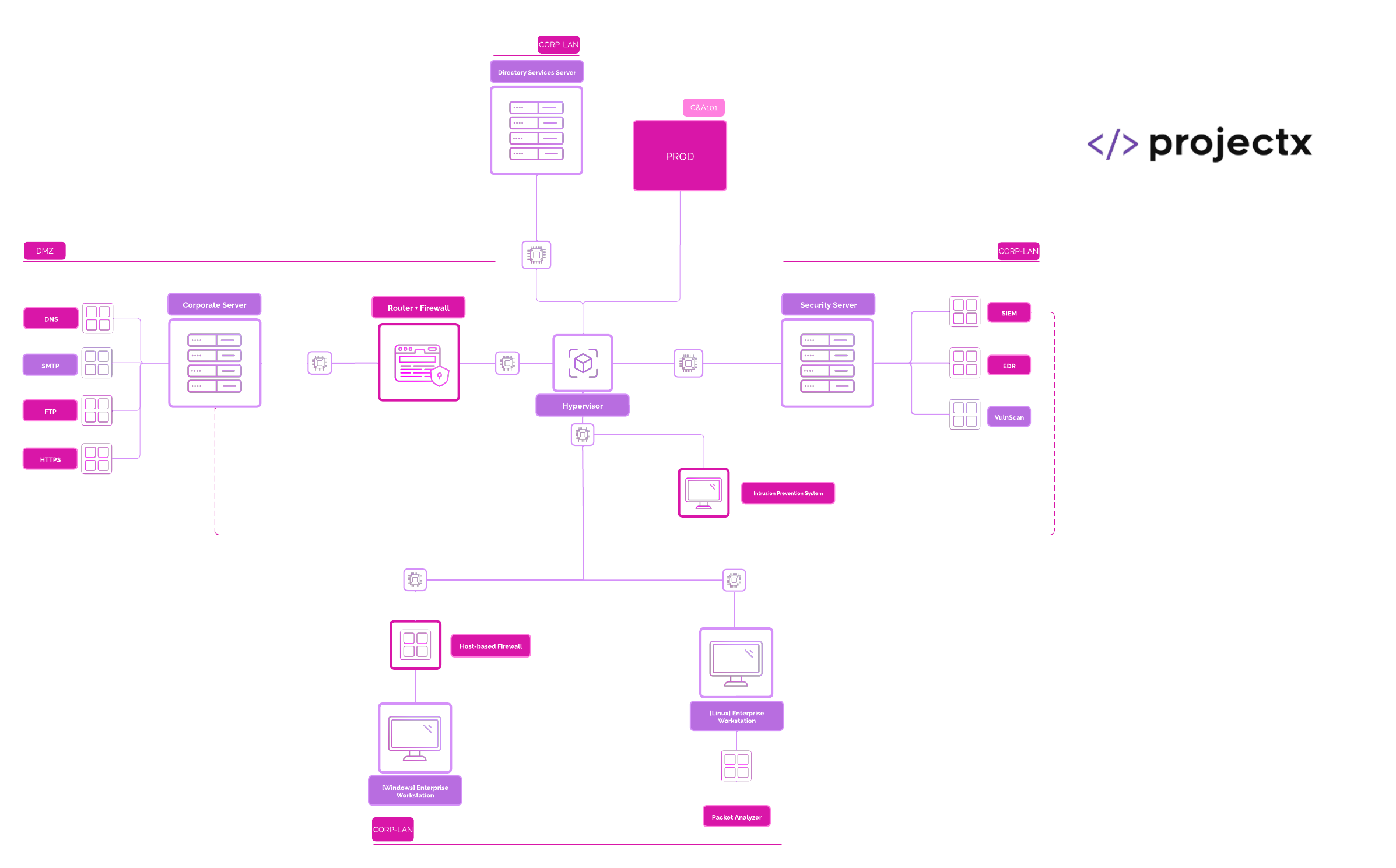
All topolgies were made with Lucidchart.
We will be configuring a few additional networks in our "Defenses" section.
VirtualBox: NAT Network
- Name:
project-x-nat(NatNetwork) -
IP Address Range:
10.0.0.0/24- Usable Range:
10.0.0.1 – 10.0.0.254 - DHCP Dynamic Scope:
10.0.0.100 – 10.0.0.200
- Usable Range:
VirtualBox: Host-only Adapter
- Name:
LAN(Host-only) -
IP Address Range:
192.168.15.0/24- Usable Range:
192.168.15.1 – 192.168.15.254 - DHCP Dynamic Scope:
192.168.15.5 – 192.168.15.10
- Usable Range:
VirtualBox: Host-only Adapter
- Name:
DMZ(Host-only) -
IP Address Range:
10.0.5.0/24- Usable Range:
10.0.5.0 – 10.0.5.10
- Usable Range:
💡 VMware Workstation Pro Support
- VMware Workstation Player is not shown during lectures, we assume VMware Workstation will work, however, we have not tested this hypervisor yet.
Attacker¶
We will be performing "ad hoc" attacks. Instead of an end-to-end attack, like we saw in Enterprise 101, each of our attack scenarios will correspond to attack tactic (the why) and technique (the how).
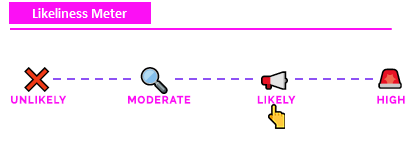
"Likeliness" Meter¶
Each attack is rated on the "Likeliness Meter" or how likely the attack is to happen in the real world.
-
Unlikely: Most likely won't happen (never say never).
-
Moderate: Has a chance of happening given certain context and dependencies (i.e. the attacker has to be on the same WiFi network).
-
Likely: Could happen, especially if certain conditions are met (and security controls have not been met).
-
High: Will likely happen given conditions (i.e. brute forcing passwords on an open SSH server).
Why?: Security training often focuses on disparate attack tactics and techniques without disclosing whether the attack would actually be real-world. As we are interested in the security components of these labs, it's important to know how likely an attack were to actually happen.
Exercise Files¶
A few exercise files are used throughout Network & Attacks 101.
1) A login page for our ProjectX Internal portal.
2) Dockerfiles and configuration files for our web, dns, and ftp containers.
You are welcomed to download these project files, the full code is also embedded in the guides.
Clone the repository: git clone https://github.com/projectsecio/exercise-files/tree/main/networks-attacks-101
Hosts¶
In addition to our original topology, we have a one extra VM and three new containers (denoted by 🌟).
| Hostname [project-x-…] | IP Address | Function | Core Section |
|---|---|---|---|
-dc (corp.project-x-dc.com) |
10.0.0.5 | Domain Controller (DNS, DHCP, SSO) | E101 |
corp-svr |
10.0.0.8 | SMTP Relay Server | E101 |
-sec-box |
10.0.0.10 | Dedicated Security Server | E101 |
-sec-work |
10.0.0.103 or (dynamic) | Security Playground | E101 |
-win-client |
10.0.0.100 or (dynamic) | Windows Workstation | E101 |
-linux-client |
10.0.0.101 or (dynamic) | Linux Desktop Workstation | E101 |
attacker |
dynamic | Attacker Environment | E101 |
🌟 corp-fw |
192.168.15.2 | Router & Firewall | NA101 |
🌟 corp-svr-web-svr |
10.0.5.10:80 | Web Server | NA101 |
🌟 corp-svr-dns-svr |
10.0.5.10:53 | DNS Server | NA101 |
🌟 corp-svr-ftp-svr |
10.0.5.10:21 | File Server | NA101 |
Changes to IP Topology¶
Networks & Attacks 101 will be broken down into two parts.
1) Infrastructure provisioning and attacks. Here, our IP addresses will stay the same as they did in Enterprise 101.
2) Defenses deployed. This is where the changes to IP addresses will change.
Our IP topology will be changing after we deploy pfSense ([project-x-corp-fw]), which will be the first defensive tool we use.
| Hostname [project-x-…] | IP Address | Function | Core Section |
|---|---|---|---|
-dc (corp.project-x-dc.com) |
192.168.15.25 | Domain Controller (DNS, DHCP, SSO) | E101 |
corp-svr |
10.0.5.10 | SMTP Relay Server | E101 |
-sec-box |
192.168.15.50 | Dedicated Security Server | E101 |
-sec-work |
192.168.15.8 or (dynamic) | Suricata | NA101 |
-win-client |
192.168.15.5 or (dynamic) | Windows Workstation | E101 |
-linux-client |
192.168.15.6 or (dynamic) | Linux Desktop Workstation | E101 |
attacker |
dynamic | Attacker Environment | E101 |
corp-fw |
192.168.15.2 (LAN) | Router & Firewall | NA101 |
corp-svr-web-svr |
10.0.5.10:80 | Web Server | NA101 |
corp-svr-dns-svr |
10.0.5.10:53 | DNS Server | NA101 |
corp-svr-ftp-svr |
10.0.5.10:21 | File Server | NA101 |
Accounts & Passwords¶
All passwords will stay the same, we will have a few new ones added (denoted by 🌟)..
| Account | Password | Host | Core Section |
|---|---|---|---|
| Administrator | @Deeboodah1! | ...-dc | E101 |
| [email protected] | @password123! | ...-win-client | E101 |
| janed@linux-client | @password123! | ...-linux-client | E101 |
| project-x-sec-work | @password123! | ...-sec-work | E101 |
| sec-work@sec-box | @password123! | ...-sec-box | E101 |
| project-x-admin@corp-svr | @password123! | …-corp-svr | E101 |
| attacker@attacker | attacker | attacker | E101 |
| 🌟 admin | pfsense | ...-corp-fw | NA101 |
| 🌟 [email protected] | smile | ...-corp-svr-web | NA101 |
Downloads¶
ISOs are used to provision operating systems. There are a couple ways you can download these files.
Method 1: Preferred (if possible)¶
We will only have one additional ISO that will need to be downloaded.
Using the Sync.com Link, you can download the ISO Images directly to your computer.
- 👉 Download: Projectsecurity - Networks & Attacks 101
These ISO files contain the exact versions used when creating this program. This allows you to lock in the version, minimizing a possible mishap in the future. There may be minor updates that could change the way you get to a specific file, especially for rolling releases.
If you have a stable Internet connection, please download these files to your workstation.
There has been some trouble in past courses when using Sync, so this may not always work. If so, please continue onto Method 2.
Method 2: Direct Install¶
Download the ISO files directly from the provider. Depending on when you take this program, there could be changes to the UI. The fundamentals will stay the same.
You can download the ISO Files Using the Links:
💡 For the pfSense ISO, you will have to enter in contact details, you can add dummy information.
pfSense: https://www.pfsense.org/download/
Operating Systems¶
In addition to all VMs with Operating Systems, we will only have one new operating system.
pfSense: An open-source firewall/router platform based on FreeBSD. pfSense includes features like stateful packet inspection, VPN support (IPSec/OpenVPN), intrusion prevention, DNS filtering, and traffic shaping. Often used in enterprise or homelab environments for full control over network security and routing.
Virtual Machines (VMs)¶
VirtualBox or VMware Workstation Pro can be used as our hypervisor for virtualization.
Reference below for Virtual Machine specifications. These are important.
| VM Name | Operating System | Specs | Storage (minimum) |
|---|---|---|---|
| [project-x-corp-svr-fw] | FreeBSD | 1 CPU / 2048 MB | 50 GBs |
Tools¶
Enterprise Tools + Defense¶
Wazuh File Integrity Monitoring: Monitors files and directories for changes (like creation, deletion, or modification).
pfSense: An open-source firewall/router platform based on FreeBSD. pfSense includes features like stateful packet inspection, VPN support (IPSec/OpenVPN), intrusion prevention, DNS filtering, and traffic shaping. Often used in enterprise or homelab environments for full control over network security and routing.
Suricata: A high-performance, open-source IDS/IPS and network security monitoring engine. It inspects network traffic using deep packet inspection, supports rule-based detection (like Snort rules), and can drop or alert on suspicious activity such as C2 traffic, port scans, or exploits.
Active Directory GPO: GPOs allow administrators to centrally manage and configure operating systems, applications, and user settings in an AD environment.
Windows Firewall: A built-in host-based firewall that filters inbound and outbound traffic based on rules.
Wireshark: A GUI-based network protocol analyzer used for packet capture and deep inspection of network traffic. It's commonly used for troubleshooting, malware analysis, and understanding protocol behavior (e.g., HTTP, DNS, TLS, etc.).
tcpdump: A CLI-based packet capture tool used to monitor and analyze network traffic in real-time. It's ideal for lightweight, remote analysis or automation and can be scripted easily.
Offense¶
hping3: A command-line packet crafting tool often used for network scanning, firewall testing, or DoS attacks. You can forge TCP/IP packets to mimic or manipulate connections (e.g., SYN floods, spoofed pings). It’s popular in recon and network stress testing.
NetImposter: A man-in-the-middle (MitM) attack tool used to impersonate trusted services over the network. Often used in LAN environments to impersonate login portals or network services to capture credentials or inject malicious payloads.
CVE-2011-2523: A backdoor vulnerability in a maliciously modified version of vsftpd 2.3.4, which was not an official release from the vsftpd project.
Hashcat: A powerful password recovery and cracking tool that uses GPU acceleration for fast cracking of password hashes. Supports a wide variety of hash formats (MD5, SHA, NTLM, bcrypt, etc.) and attack modes (dictionary, brute-force, rule-based, hybrid).
Ettercap: A network sniffer and MitM attack tool that supports ARP spoofing, packet injection, and credential harvesting. It can intercept and manipulate network traffic in real time—especially dangerous in unsegmented networks without encryption.
Guides Numerical Order¶
The numerical order for the step-by-step guides is already in place based on the navigation menu. These guides serve as the basis for the project. It is recommended the respective guide docs page is opened while following along in the program.
👉 If you prefer to follow content by reading, these guides on this docs site will provide the same information as the video lectures.
Guides¶
Guides Format
The screenshots always conform to step in text, then screenshot evidence below it.

We hope you enjoy this core section!
Made with ♥ by ProjectSecurity.io.