Deploy DoS Attack
Prerequisites¶
- VirtualBox or VMware Workstation Pro Installed.
- Virtual Machine
[project-x-corp-svr]is configured with Docker. - Docker Container
[project-x-corp-svr-web-svr]setup and configured. - Virtual Machine
[project-x-attacker]is turned on.
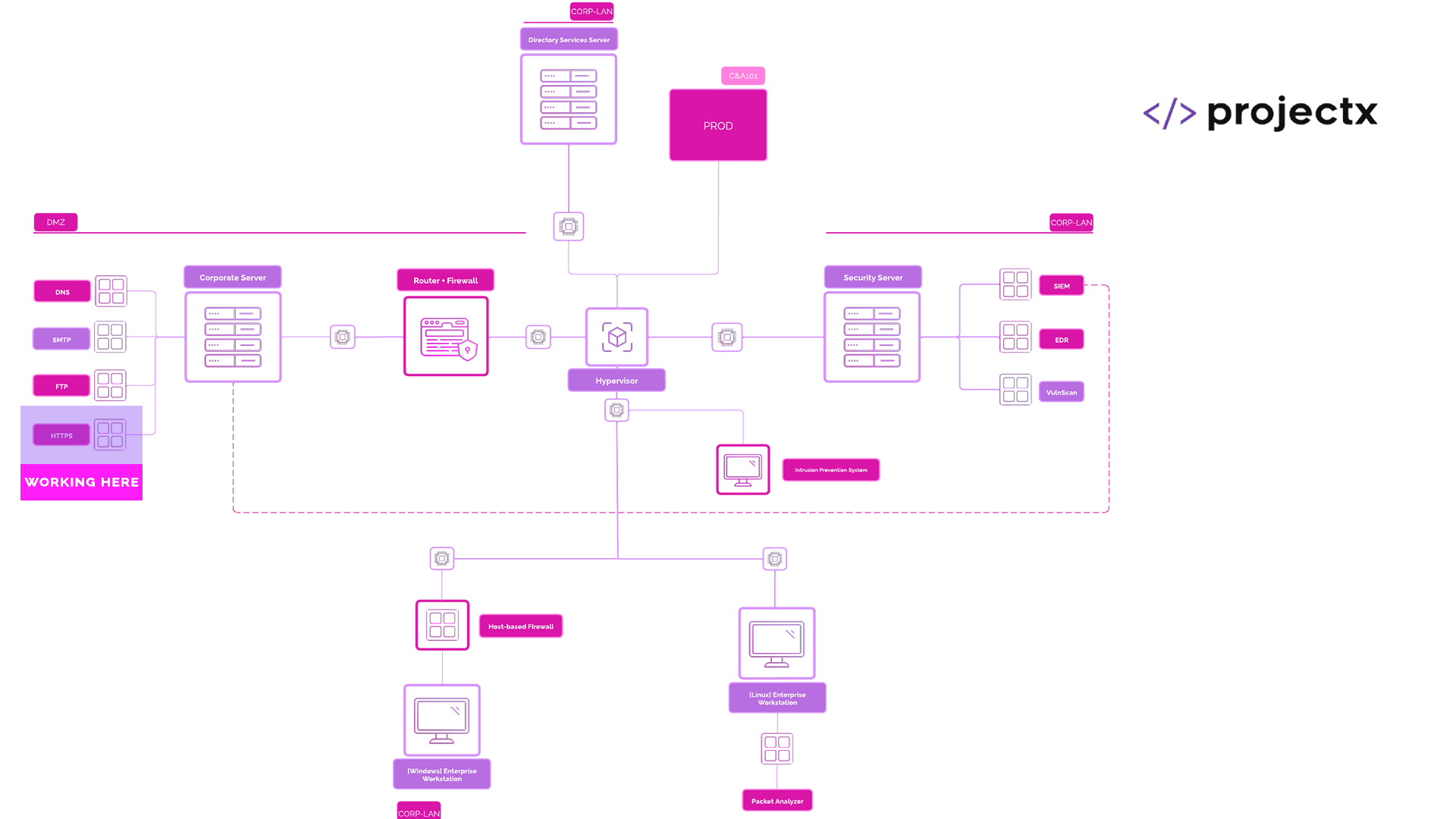
Network Topology¶
Likeliness Meter¶
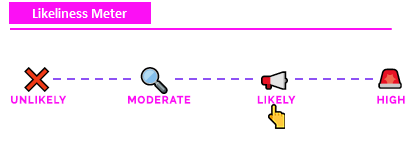
Likely: Depending on a companies digital footprint and reliance to online operations (most companies have some dependencies), Distributed Denial of Service (DDoS) attacks will occur. Attackers like to use DDoS as a means to interupt the availability and operations of their victims. A singular Denial of Service (DoS) attack is not as common and would likely impact up to a few hosts.
Denial of Service Attacks Overview¶
A Denial of Service (DoS) attack aims to overwhelm a system, network, or service with excessive traffic or resource exhaustion, making it unavailable to legitimate users.
There are a couple types of DoS.
- Denial of Service (DoS): Typically originates from a single source, such as a computer or server. Typically looks to overwhelm another computer.
- Distributed Denial of Service (DDoS): These attack leverage a large number of compromised devices—often part of a botnet to overwhelm a resource, such as a web application or service.
How is DoS accomplished?¶
DoS and DDoS attacks can be deployed in many different ways.
A few high-level ones include.
Common Types of DDoS Attacks 1. Volume-Based Attacks: Overwhelm the target with so many requests that it exhausts all bandwidth and crashes. Example: UDP floods, ICMP floods, DNS amplification.
-
Protocol Attacks: Use protocol weaknesses to deploy attack. Example: SYN floods, fragmented packet attacks, Ping of Death.
-
Application Layer Attacks: Use Layer 7 protocols such as HTTP to send so many requests that it crashes the web server. Aim: Crash or slow down application services Example: HTTP GET/POST floods.
We will be using a technique called SYN Flood. Although this attack is fairly unsophisticated, it can be successful for small targets.
SYN Flood Technique¶
A SYN Flood is a type of Denial of Service (DoS) attack that targets the TCP handshake process.
It exploits the way TCP establishes connections by sending a large number of SYN (synchronize) requests to a target server, without completing the handshake.
Here's a basic overview of how the SYN Flood technique works:
- The attacker sends a flood of TCP SYN packets to the target.
- The target replies with SYN-ACK responses and allocates resources for each connection.
- The attacker either doesn’t respond with the final ACK or sends spoofed SYNs from unreachable IP addresses.
- The target waits for the final ACK, leaving half-open connections in memory.
- The backlog queue of pending connections fills up, preventing legitimate users from connecting.
Impact¶
DoS and DDoS can lead to service downtime, loss of availability. This can lead to a loss of trust by customers and increased operational costs.
DoS Attack Using hping3¶
Container¶
If web-svr is currently running, stop with docker stop web-svr.
We are going to create another docker container called projectxwebdos, except with limitions.
With the power of Docker, we can specify the resources allocated to a container to the --cpus and --memory settings. This will allow us to "simulate" a web server that has limited resources.
We can issue a command like the following:
docker run -d \
--name projectxwebdos \
--network host \
--cpus="0.25" \
--memory="6m" \
projectx-nginx
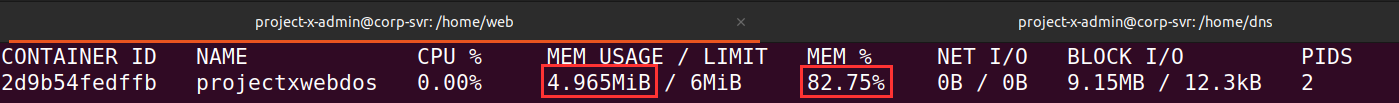
We can inspect the docker containers current network and I/O usage with the docker stats command. Once we launch our DoS, you will see the stats start to increase.
docker stats web-svr.
[project-x-attacker]¶
So how can we launch the SYN Flood attack?
Luckily, we have many tools at our disposal as attackers. If you Google search "DoS attack tools", you will find a very popular command line tool call hping3.
hping3 is a packet crafting tool that allows us to send various types of network requests using various settings.
We can specify a port to target with -p, the type of packets with -S, the delay of when to send packets with -i, the number of packets to send -c.
We can also have hping3 run indefinitely. You got options.
- If you take away the
-coption,hping3will run until you manually stop.
Let's craft something like the following:
sudo hping3 -i u10 -S -p 80 -c 250000 10.0.0.8
Going back to the docker container, we can start to see the uptick.
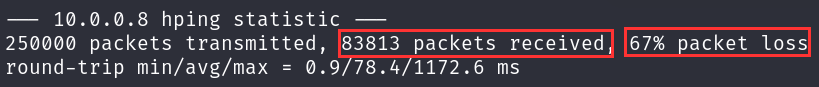
If wait for all 250,000 packets to send, we can see the percentage of packet loss. This means we are beginning to overwhelm the target, we are asking for more than it can handle.
That's about it for this attack. Unfortunately, we won't be able to overwhelm our projectxwebdos container enough to the point where we could no longer load the web page.
Play around with hping3.
You are welcomed to delete the projectxwebdos once you are finished or keep it around.
docker stop web-svr.docker rm web-svr.