Perform Credential Stuffing (Exercise)
Prerequisites¶
- VirtualBox or VMware Workstation Pro Installed.
- Virtual Machine
[project-x-win-client]is turned on and configured. - Virtual Machine
[project-x-attacker]is turned on.
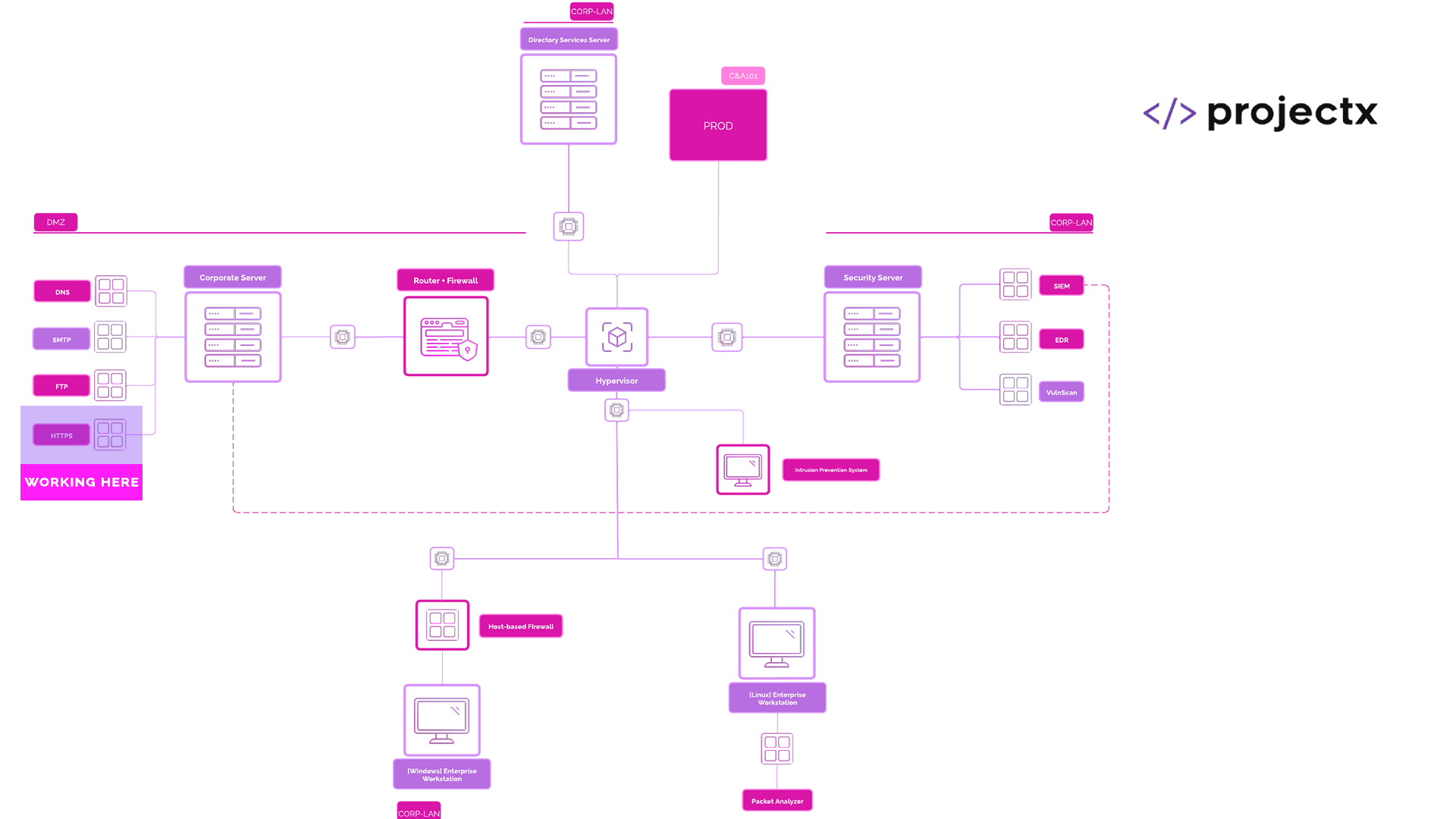
Network Topology¶
Likeliness Meter¶
High: Attackers will use credential stuffing as part of their technique arsenal. Password reuse is very common. Using known credentials from previous data breaches or leaks will lead attackers to land greater success rates in gaining access to accounts.
Credential Stuffing¶
We have conducted a few password-based attacks in the past.
Credential stuffing is yet another iteration of password-based attacks.
Many of us are lazy. More passwords equals remembering stuff that we don't feel like doing.
So, guess what happens... we reuse the same passwords.
Attackers take advantage of our laziness to deploy credential stuffing attacks.
Credential stuffing is a type of cyber attack where attackers use stolen username and password combinations—typically obtained from data breaches to try to gain unauthorized access to other accounts.
Since many people reuse passwords across multiple sites, these attacks rely on automation to quickly test large volumes of credentials on different services. Successful logins can lead to account takeovers, data theft, or further exploitation.
Lesson, don't reuse passwords. And be lazy in other areas of your life, not passwords.
There are some great resources out there to help us make sure our accounts stay secure, such as password managers, and services to help us verify our accounts have not been compromised.
HaveIBeenPwned¶
Have I Been Pwned (HIBP) is a free online service that helps individuals and organizations determine if their personal data—such as email addresses or passwords—has been exposed in known data breaches. Created by cybersecurity expert Troy Hunt in 2013, the platform aggregates and analyzes data from hundreds of breaches, encompassing billions of compromised accounts.
This is a great place to gather email addresses that have been compromised.
Attackers can use this to their advantage. If they have email addresses, they enter them into HIBP to see if and where the email has been compromised.
Credential Stuffing John Doe's Account¶
We have already seen passwords attacks in the Enterprise 101 Core Section.
Since this is a simulated environment, we won't actually have [email protected] in a data compromise.
We could simulate credential stuffing by assuming this email address has been compromised. And let's assume we were able to gather the known password hash list from this compromise.
Let's attempt to crack this account's hash. We could then use this password to log into Project X's corporate page.
A real password hash list would be thousands if not millions of lines lone depending on the number of users.
For the sake of time savings, we are going to act as if we got the hash list and we found [email protected] with an associated hash.
[email protected]:3ddaeb82fbba964fb3461d4e4f1342eb
Let's attempt to see if we can crack John's hash from this website's data breach.
To crack hashes, we can use hashcat. A very popular tool used in the penetration testing community.
Hashcat is a powerful, open-source password recovery and cracking tool designed for password hash attacks.
- Because our VM only has 2 GB of RAM assigned, you will not be able to run modern versions of hashcat.
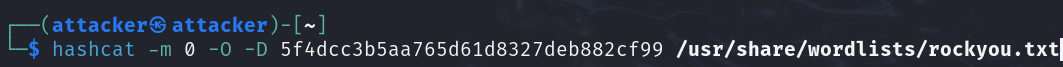
With hashcat, we can specify the mode or hash algorithm with (-m) and the password list, in this case the standard rockyou.txt.
hashcat -m 0 5f4dcc3b5aa765d61d8327deb882cf99 /usr/share/wordlists/rockyou.txt
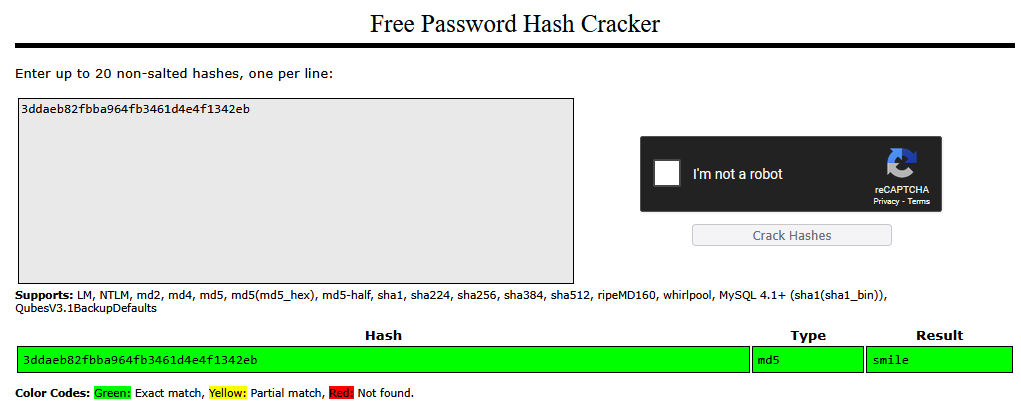
If hashcat does not work, we can also use an online Hash Cracker, such as Crackstation.
Entering the hash into Crackstation.net, we should see the password and hash type, which is MD5.
Let's attempt to log into the projectxcorp.com domain using John's account.
Makes sure
[projectx-corp-svr]is powered on and theweb-svrcontainer is running.Make sure both machines are on the
project-x-network, Nat Network.
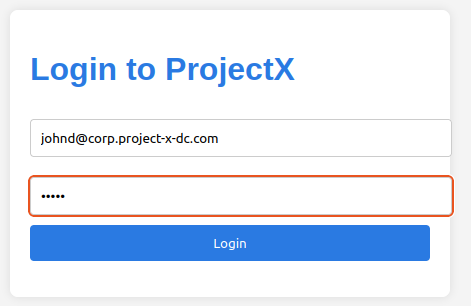
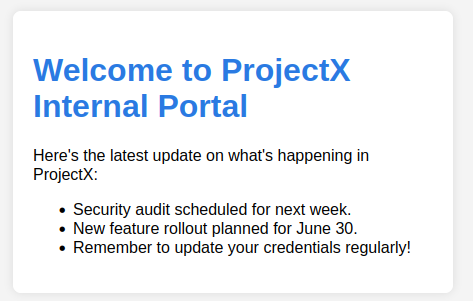
Looks like we were able to get in, success!
Real-world Application¶
This was a very selective scenario. In the real-world, attackers will acquire large lists of known compromised accounts. They can receive plaintext or hashed passwords, along with their associated usernames, depending on the type of data that was compromised.
They will then use this data to target other services, such as emails, corporate accounts, social media, and more.