Provision & Setup Security Onion
Prerequisites¶
- Virtualbox or VMware Workstation Pro installed.
- Virtual Machine with Security Onion ISO has been downloaded and provisioned (the ISO should be attached to the new VM).
- Security Onion Virtual Machine has at least 50.00 GB of dynamic storage available.
- Windows Server 2025 with AD Directory Services (ADDS) configured and turned on.
Network Topology¶
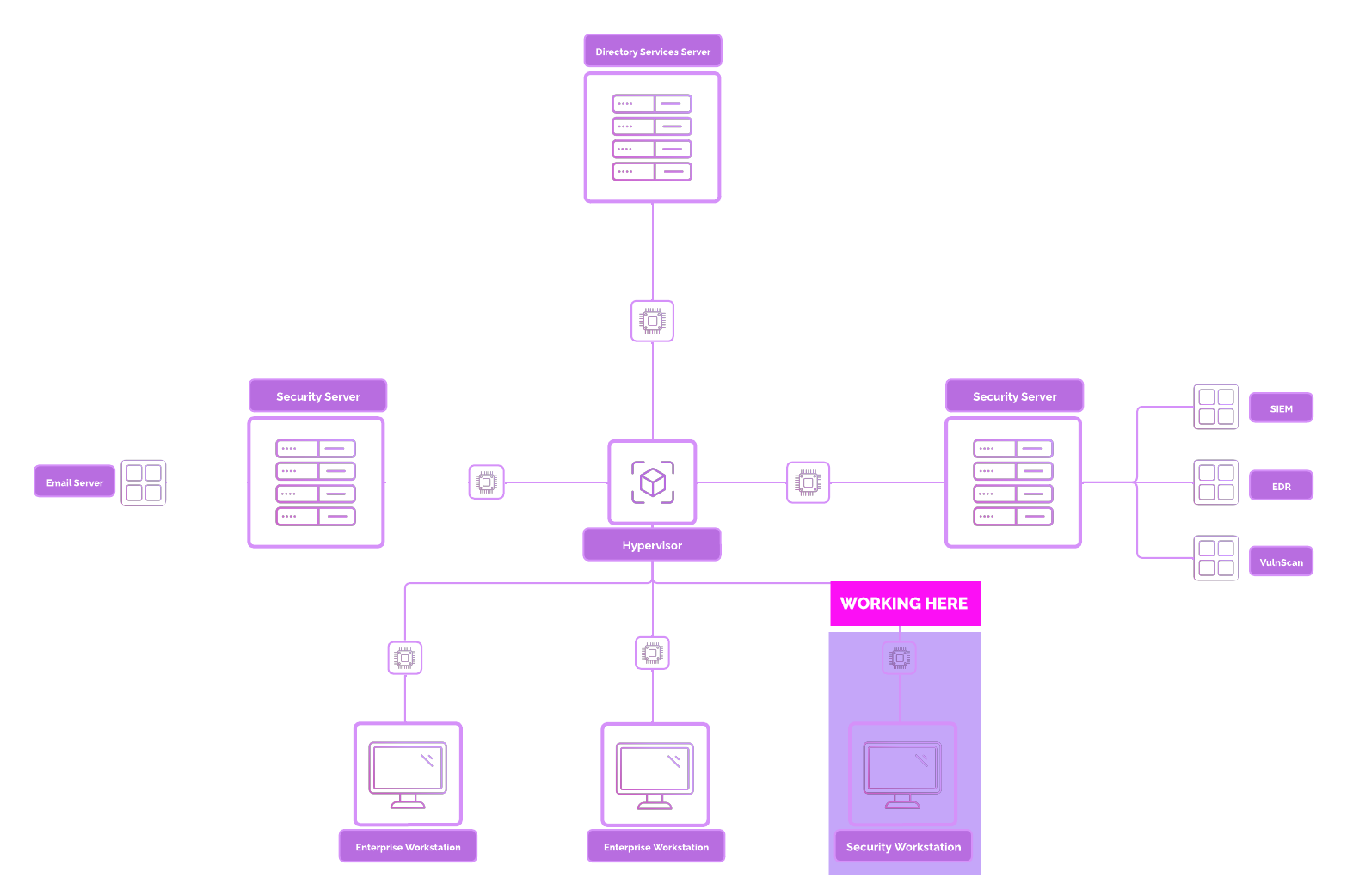
Note
The the Enterprise 101 Core Section, we do not use Security Onion. Security Onion will be used in Networks & Attacks 101. So you do not have to do this.
Security Onion Overview¶
What is Security Onion?¶
Security Onion is a free, open-source platform for network security monitoring (NSM), log management, and intrusion detection. It provides a comprehensive suite of tools designed to help analysts detect, investigate, and respond to cyber threats in real time.
Think of Security Onion as the Kali Linux of network monitoring. It comes preconfigured with tools such as:
- Zeek (formerly Bro): Network traffic analysis.
- Suricata: Intrusion detection and prevention. We will use this eventually!
- Elastic Stack (Elasticsearch, Logstash, Kibana): Log management and analysis.
How is Security Onion Used?¶
Security Onion can be deployed as part of the business network, under security or the network team for multiple reasons.
Network Security Monitoring (NSM)
- Packet Capture and Analysis: Tools like Zeek analyze network traffic for anomalies or suspicious activity.
- Intrusion Detection Systems (IDS): Suricata performs real-time deep packet inspection to identify malicious activity.
Log Management and Analysis
- Collects and aggregates logs: from endpoints, firewalls, servers, and other devices for network visibility.
- Elastic Stack: enables querying, visualizing, and analyzing logs in an intuitive dashboard.
Incident Response
- Alerts and Correlation: Generates alerts for suspicious activities, helping analysts prioritize threats.
- Threat Hunting: Analysts can proactively search for signs of compromise using enriched datasets.
Security Implications¶
Security Onion enhances an organization’s security posture with advanced detection and monitoring capabilities:
- Proactive Threat Detection: Identifies threats before they escalate and cause damage, if the tools are properly deployed.
- Comprehensive Visibility: Aggregates network and endpoint data for a holistic view.
- Incident Response Readiness: Equips analysts with tools for quick investigation and response.
💡 Best Practice: Keep Security Onion servers isolated to minimize the risk of compromise.
Setup Security Onion¶
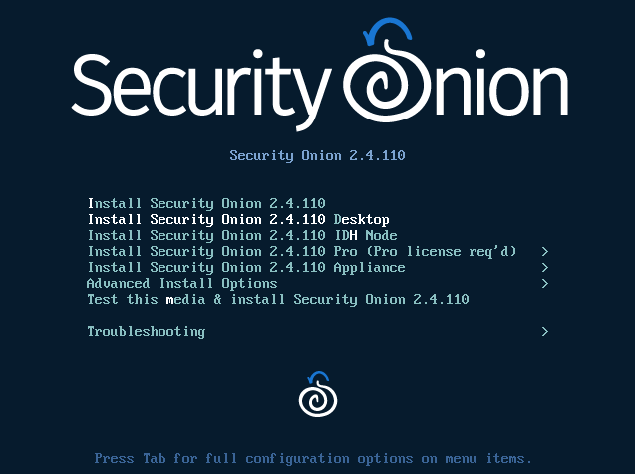
Navigate to “Install Security Onion 2.4.110 Desktop” and press Enter.
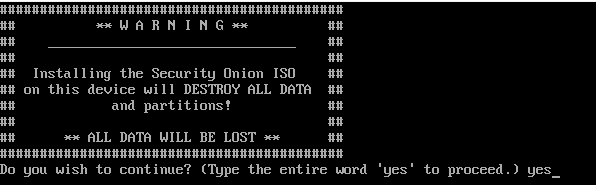
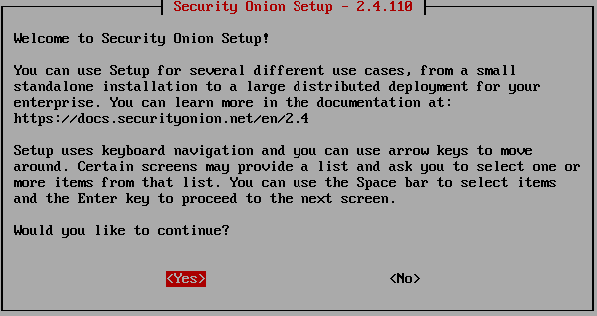
Type Yes and press Enter.
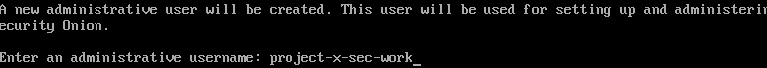
Create a new administrator account:
- Username:
project-x-sec-work - Password:
@password123!
👉 Refer to the “Project Overview” guide for more information on default usernames and passwords.
Allow the system to install (this may take a few minutes).
Once completed, press Enter.
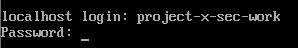
Let the VM reboot and enter the username and password.
- Username:
project-x-sec-work. - Password:
@password123!.
Select “Yes” when prompted.
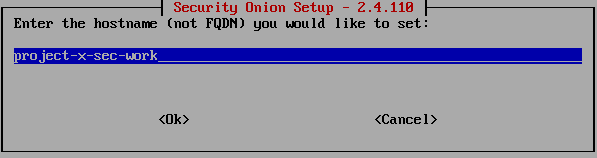
Enter the following hostname.
project-x-sec-work.
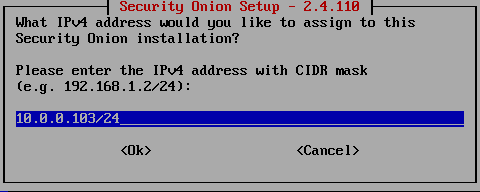
Press Enter until you reach the IPv4 address setup.
- IP Address:
10.0.0.103/24
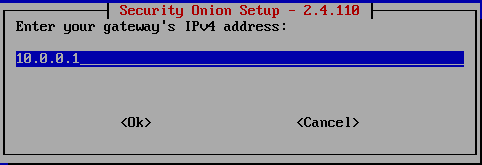
- Default Gateway:
10.0.0.1
Accept the default DNS servers.
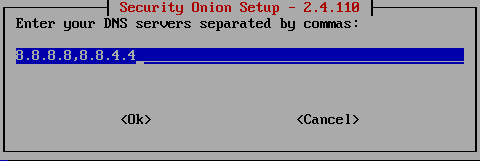
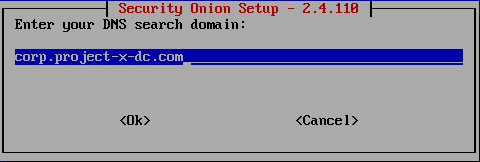
Add the following DNS entry:
corp.project-x-dc.com
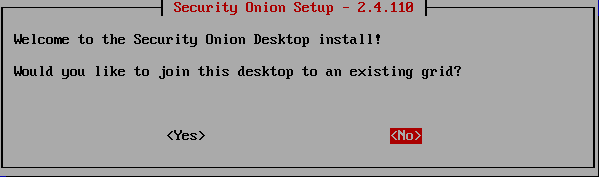
Select the default “No”, then press Enter.
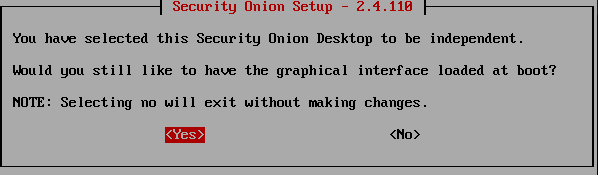
Use the Left Arrow Key to select “Yes”, then press Enter.
The graphical menu will close and return to the terminal. Restart the machine by running:
Success! Log into Security Onion.

Open a new terminal session. Right-click the desktop, select "Open in Terminal".
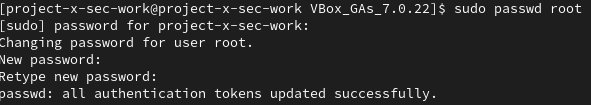
Issue the following command to change the root password to (@password123!).
sudo passwd root
📷 Take Snapshot!