Setup The Attacker Machine
Prerequisites¶
- VirtualBox or VMware Workstation Pro Installed.
- Virtual Machine with Kali Linux ISO has been downloaded and provisioned (the ISO should be attached to the new VM).
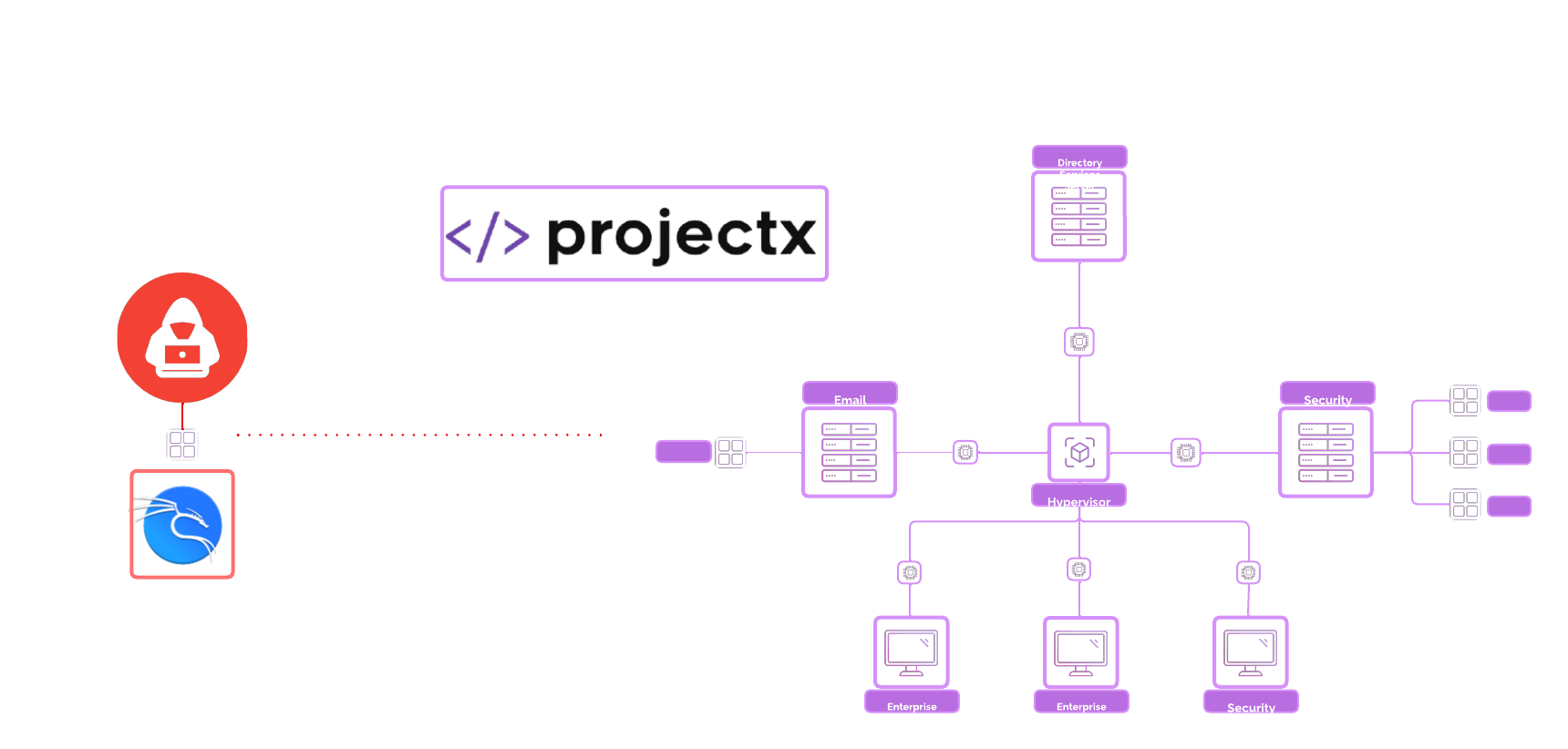
Network Topology¶
Kali Linux Overview¶
What is Kali Linux?¶
Kali Linux is a specialized Linux distribution tailored for cybersecurity professionals and ethical hackers.
Developed by Offensive Security, it is a Debian-based operating system preloaded with tools designed for penetration testing, ethical hacking, and digital forensics. Kali Linux is widely used for assessing system vulnerabilities, testing network security, and investigating cyber incidents.
Kali comes with a suite of security tools to assist in the operations.
How is Kali Linux Used?¶
Kali Linux serves multiple purposes in the cybersecurity field, including:
- Penetration Testing: Professionals use Kali Linux to simulate real-world cyberattacks and identify vulnerabilities in systems, networks, and applications. Tools like Metasploit and Burp Suite are often employed in these scenarios.
- Vulnerability Assessment: It provides tools to scan and identify weaknesses in infrastructure, ensuring they are addressed before exploitation.
- Cybersecurity Training: Kali Linux is widely used in cybersecurity training programs, competitions, and certifications.
Security Implications¶
Leveraging an operating system like Kali Linux carries certain benefits and risks.
Benefits
- Can be used by trained professionals to help understand their organizational security controls and identify vulnerabilities before actors can exploit them.
- Offers a platform to safely practice offense security techniques in controlled environments.
- Tools are aggregated in one centralized ecosystem.
Risks
- This tool can also be used maliciously by attackers if accessed by unauthorized individuals.
- Kali Linux is not meant to be a production environment without isolation. Be careful.
Configure Kali Linux¶
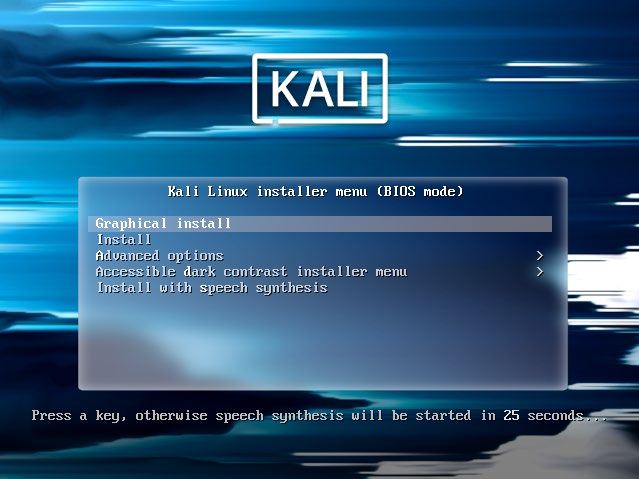
Choose the default “Graphical install”.
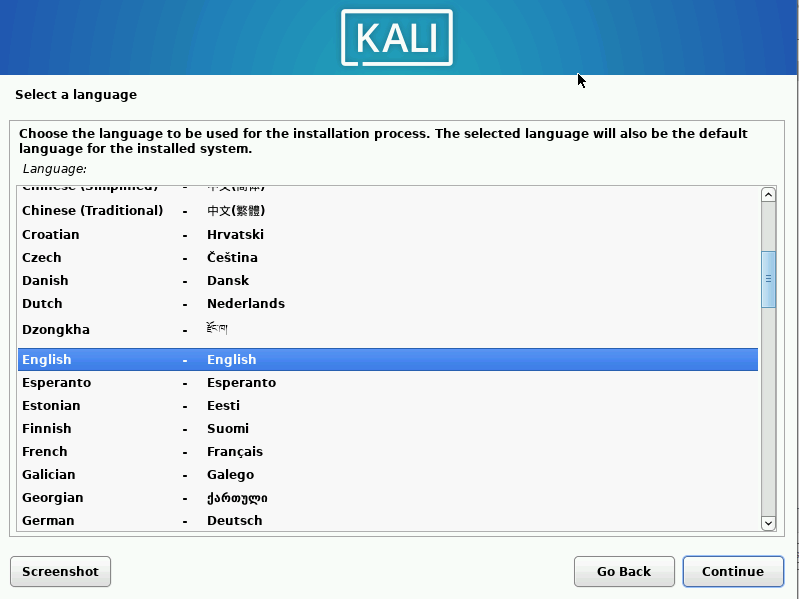
Choose Language ➔ “Continue”.
Choose the Country and Keyboard layout.
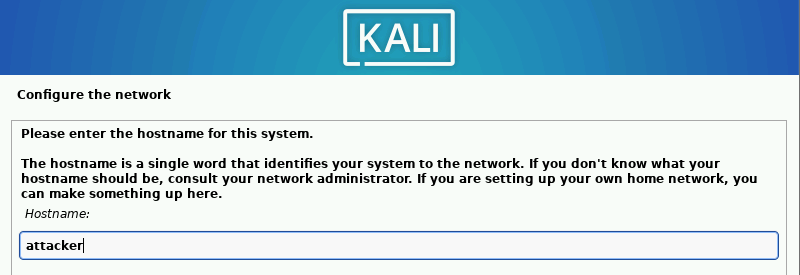
Change the hostname from kali to attacker ➔ “Continue”.
👉 Refer to the “Project Overview” guide for more information on default usernames and passwords.
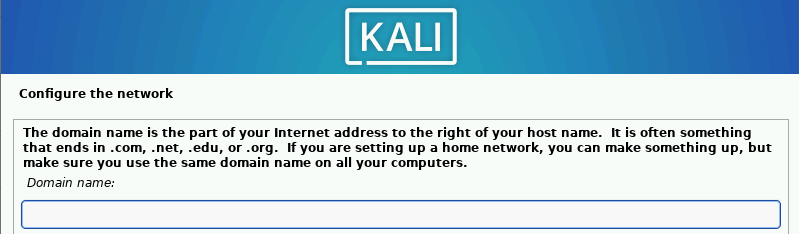
Leave the domain name empty ➔ “Continue”.
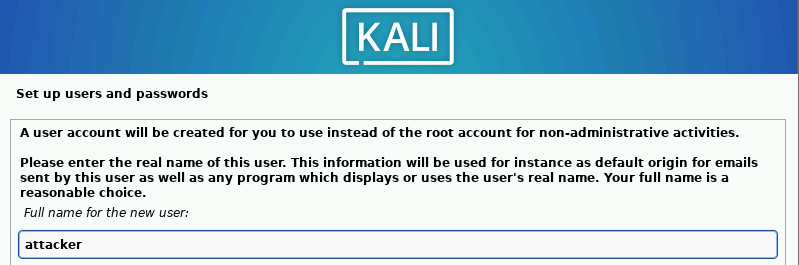
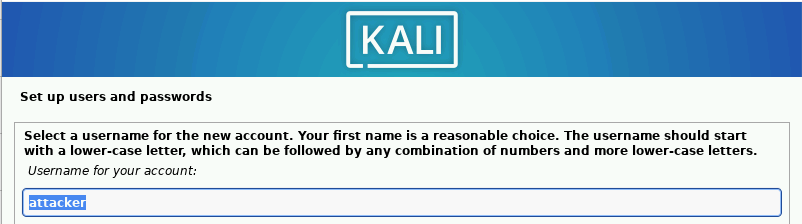
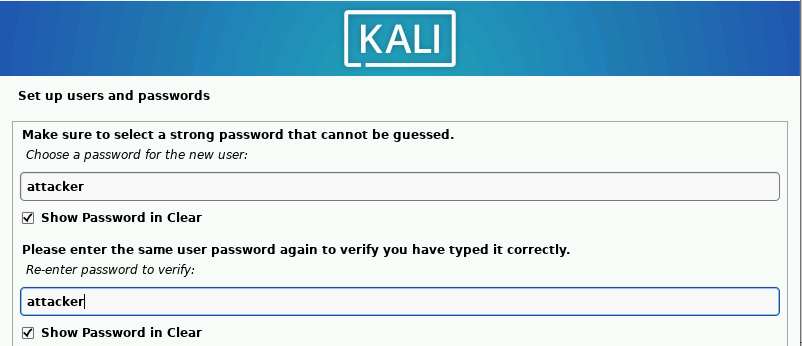
Add attacker as the new user and username.
Enter attacker as the default password ➔ “Continue”.
Choose time zone of your choice for the clock option ➔ “Continue.”
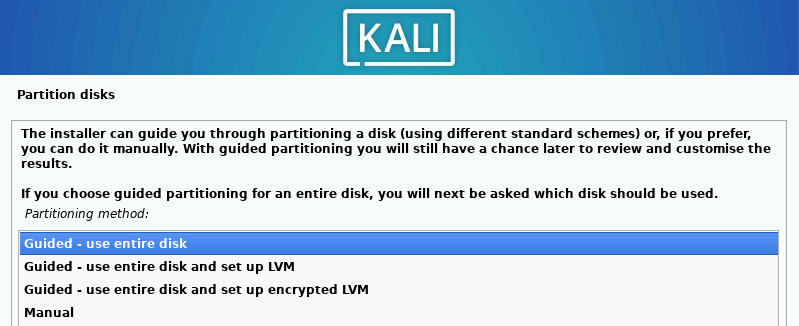
Select “Guided – use entire disk” ➔ “Continue.” Keep all defaults selected.
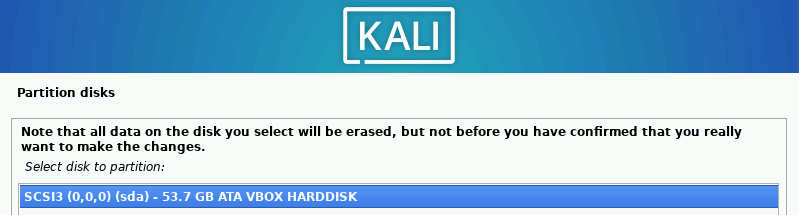
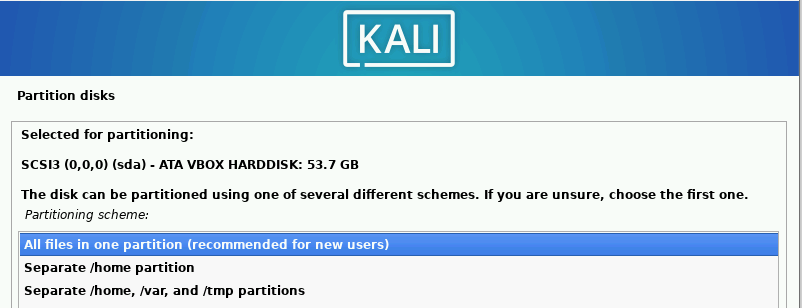
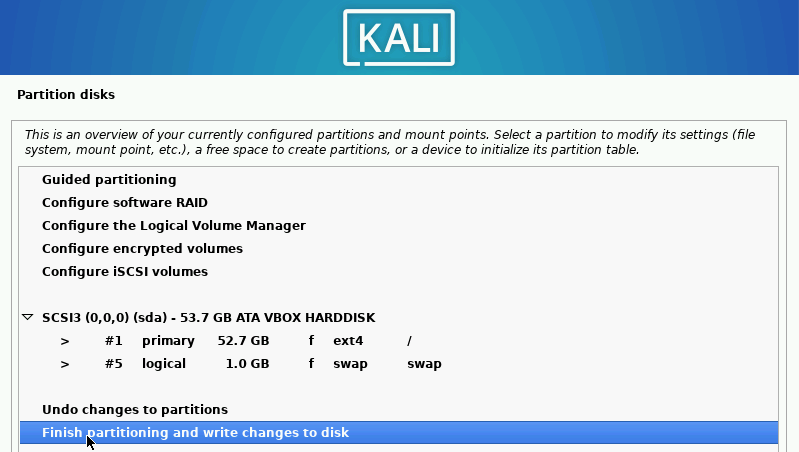
Change “Write the changes to disks?” to “Yes” ➔ “Continue.”

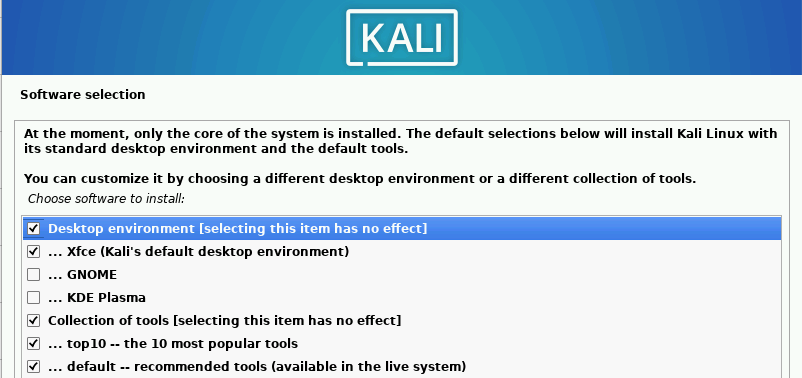
Keep defaults selected ➔ “Continue”. Wait for the software to install.
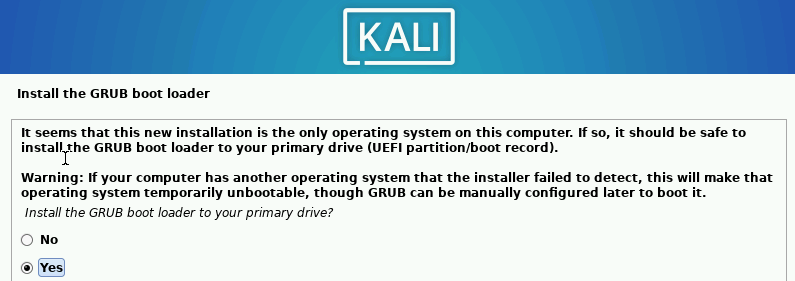
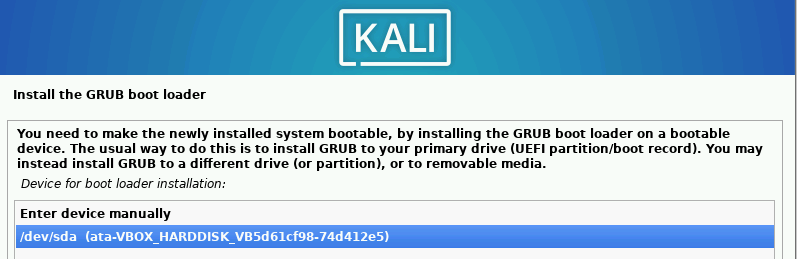
Install the GRUB Loader.
Select “Continue” and allow the system to reboot.
Login as the under the attacker account.

Success!
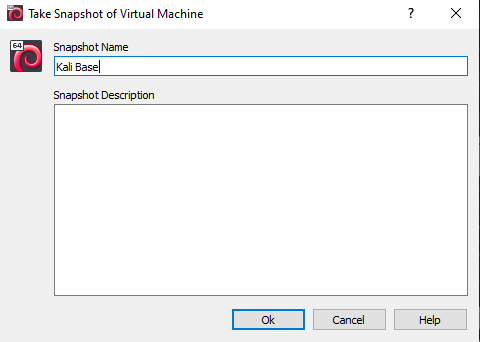
📷 Take Snapshot!
Optional¶
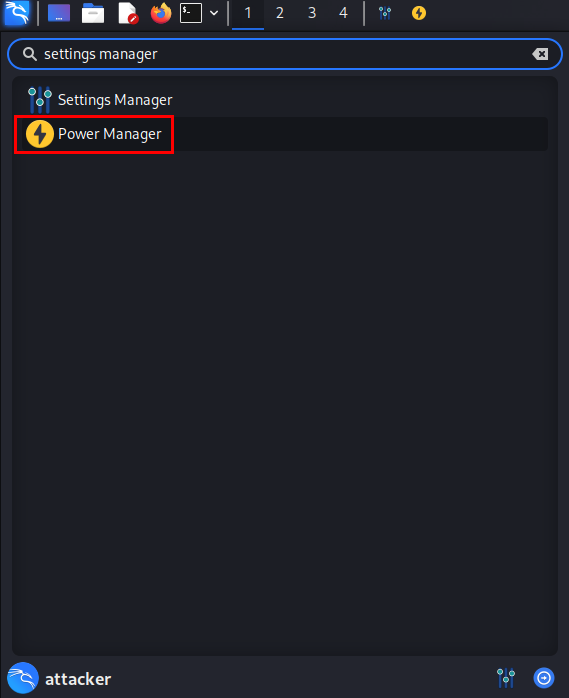
Disable Default Logoff (Timeout After 5 Minutes)¶
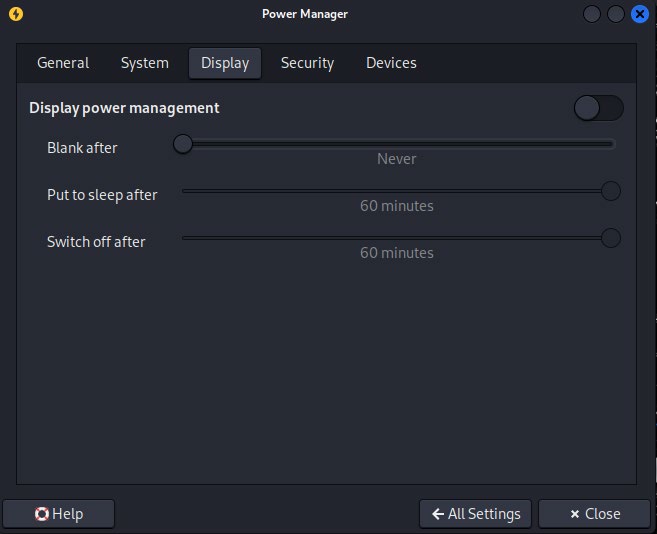
Go to the Menu Bar ➔ “Power Manager”.
Navigate to “Display” tab ➔ Drag Toggle to the left.