Overview
Project Overview¶
Welcome to Enterprise 101 - From Initial Access to Breached.
This course, referred to as a "Core Section", is all about getting you up and running with a starter homelab.
Inside the homelab, we will simulate components of a business network.
The Overview Guide is here to help outline pertinent information related to this section.
Network Topologies¶
VirtualBox: NAT Network
- Name:
project-x-nat(NatNetwork) -
IP Address Range:
10.0.0.0/24- Usable Range:
10.0.0.1 – 10.0.0.254 - DHCP Dynamic Scope:
10.0.0.100 – 10.0.0.200
- Usable Range:
VMware Workstation Pro: VMnet (NAT-enabled)
- Name:
project-x-nat(VMNet8) -
IP Address Range:
10.0.0.0/24- Usable Range:
10.0.0.1 – 10.0.0.254 - DHCP Dynamic Scope:
10.0.0.100 – 10.0.0.200
- Usable Range:
Attacker¶
Cyber Attack Simulation¶
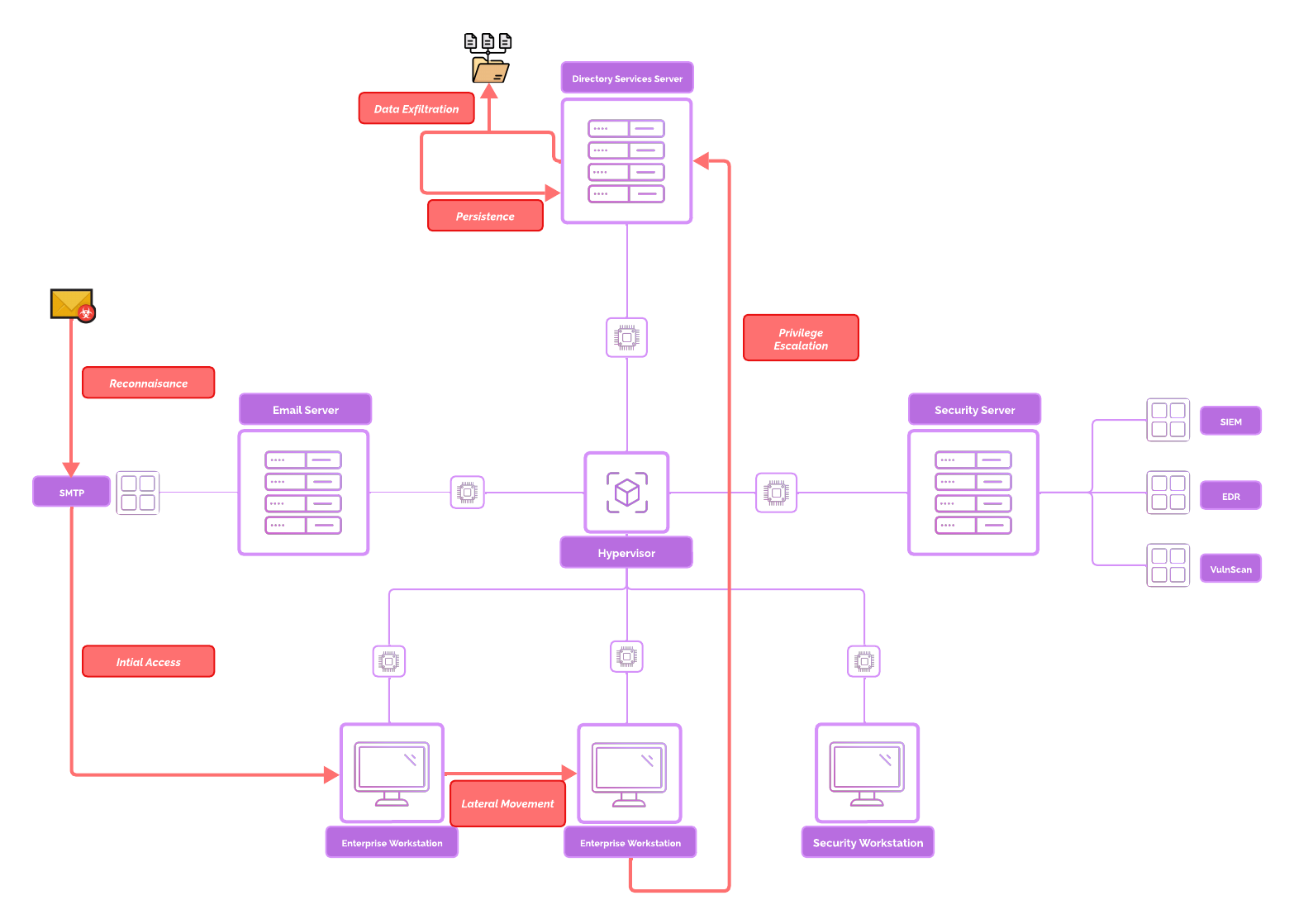
Exercise Files¶
A few exercise files are used throughout the Cyber Attack scenario.
1) A phishing website to gather user credentials.
2) A basic Powershell reverse shell.
You are welcomed to download these project files if you want to follow along.
https://github.com/collinsmc23/projectsecurity-e101
Clone the repository: git clone https://github.com/collinsmc23/projectsecurity-e101.git
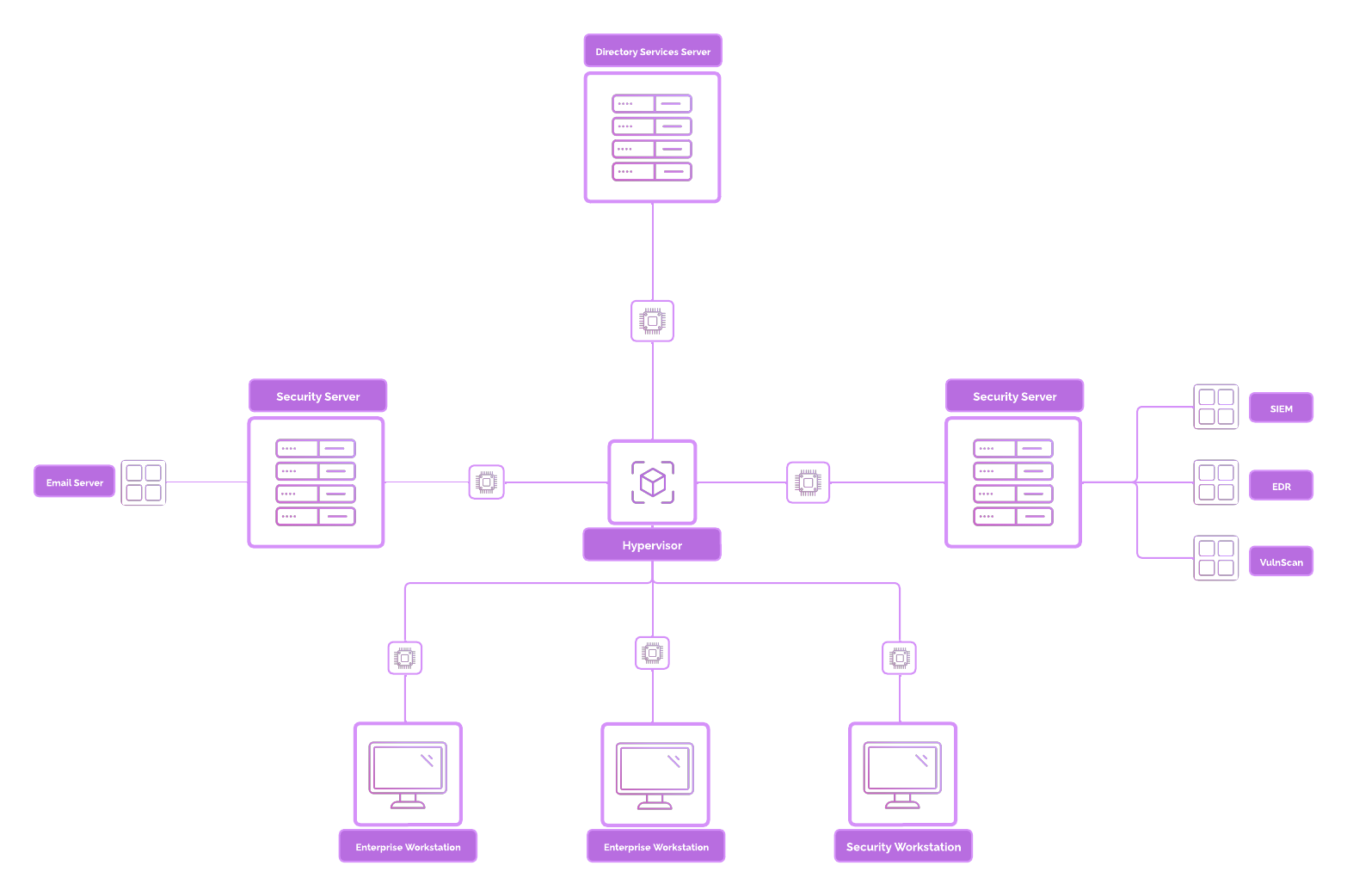
Hosts¶
| Hostname [project-x-…] | IP Address | Function |
|---|---|---|
-dc (corp.project-x-dc.com) |
10.0.0.5 | Domain Controller (DNS, DHCP, SSO) |
-admin |
10.0.0.8 | Corporate Server |
-sec-box |
10.0.0.10 | Dedicated Security Server |
-sec-work |
10.0.0.103 or (dynamic) | Security Playground |
-win-client |
10.0.0.100 or (dynamic) | Windows Workstation |
-linux-client |
10.0.0.101 or (dynamic) | Linux Desktop Workstation |
attacker |
dynamic | Attacker Environment |
Accounts & Passwords¶
| Account | Password | Host |
|---|---|---|
| Administrator | @Deeboodah1! | ...-dc |
| [email protected] | @password123! | ...-win-client |
| janed@linux-client | @password123! | ...-linux-client |
| project-x-sec-work | @password123! | ...-sec-work |
| sec-work@sec-box | @password123! | ...-sec-box |
| project-x-admin@corp-svr | @password123! | …-corp-svr |
| attacker@attacker | attacker | attacker |
Downloads¶
ISOs are used to provision operating systems. There are a couple ways you can download these files.
Method 1: Preferred (if possible)¶
Using the Sync.com Link, you can download the ISO Images directly to your computer.
- 👉 Download: https://ln5.sync.com/dl/831828380#cbtjtrs7-yhmjd4ad-yaxm6hka-x97b3ug7
These ISO files contain the exact versions used when creating this program. This allows you to lock in the version, minimizing a possible mishap in the future. There may be minor updates that could change the way you get to a specific file, especially for rolling releases.
If you have a stable Internet connection, please download these files to your workstation.
There has been some trouble in past courses when using Sync, so this may not always work. If so, please continue onto Method 2.
Method 2: Direct Install¶
Download the ISO files directly from the provider. Depending on when you take this program, there could be changes to the UI. The fundamentals will stay the same.
You can download the ISO Files Using the Links:
💡 For the Microsoft ISOs, you will have to enter in contact details, you can add dummy information.
Windows Server 2025: https://info.microsoft.com/ww-landing-evaluate-windows-server-2025.html?lcid=en-us&culture=en-us&country=us
Windows 11 Enterprise: https://info.microsoft.com/ww-landing-windows-11-enterprise.html
Ubuntu Desktop 22.04: https://releases.ubuntu.com/jammy/
Ubuntu Server 22.04: https://releases.ubuntu.com/jammy/
Security Onion: https://securityonionsolutions.com/software
Kali Linux 2024.4: https://www.kali.org/get-kali/#kali-installer-images
Operating Systems¶
👉 Alternative Methods
- Due to Windows 11 / Server 2025 system requirements, such as TPM 2.0, you download, connect, and supplement a Windows 10 workstation or Windows Server 2022 instead.
- Download the ISOs on the Microsoft Evaluation Center.
Windows Server 2025: Designed to support enterprise-level applications and network management, and identity management. This will be used as the directory services server, acting as the central hub for network connection.
Windows 11 Enterprise: Desktop operating system optimized for everyday productivity. Most common operating system used in business environments for employees. This will be used to simulate a business user.
Ubuntu Desktop 22.04: General-purpose desktop. Commonly used for software development. This will be used to simulate an enterprise software development environment.
Security Onion: An open-source platform for security monitoring, log analysis, and intrusion detection, used by cybersecurity professionals to detect, investigate, and respond to network threats and incidents.
Ubuntu Server 2022: A Linux server operating system widely used for hosting applications, databases, and web services. This will be used as our email server.
Kali Linux: A Debian-based Linux distribution tailored for penetration testing and ethical hacking. It comes pre-installed with a wide range of tools for vulnerability assessment, exploitation, wireless testing, and digital forensics.
Virtual Machines (VMs)¶
VirtualBox or VMware Workstation Pro can be used as our hypervisor for virtualization.
Reference below for Virtual Machine specifications. These are important.
| VM Name | Operating System | Specs | Storage (minimum) |
|---|---|---|---|
| [project-x-dc] | Windows Server 2025 | 2 CPU / 4096 MB | 50 GBs |
| [project-x-win-client] | Windows 11 Enterprise | 2 CPU / 4096 MB | 80 GBs |
| [project-x-linux-client] | Ubuntu 22.04 Desktop | 1 CPU / 2048 MB | 80 GBs |
| [project-x-sec-work] | Security Onion | 1 CPU / 2048 MB | 55 GBs |
| [project-x-sec-box] | Ubuntu 22.04 Desktop | 2 CPU / 4096 MB | 80 GBs |
| [project-x-corp-svr] | Ubuntu Server 22.04 | 1 CPU / 2048 MB | 25 GBs |
| [project-x-attacker] | Kali Linux 2024.2 | 1 CPU / 2048 MB | 55 GBs |
Tools¶
Enterprise Tools + Defense¶
Microsoft Active Directory: A directory service used for managing and organizing network resources, users, and permissions in a Windows environment.
Wazuh: An open-source security monitoring platform that provides intrusion detection, log analysis, vulnerability detection, and compliance reporting.
MailHog: MailHog is a lightweight email testing tool that acts as a fake SMTP server. It captures all outgoing emails sent by applications, without delivering them to real inboxes. You can inspect emails via a web interface or API.
Offense¶
Evil-WinRM: A powerful Ruby-based Windows Remote Management (WinRM) client used by penetration testers to connect to and interact with Windows systems, often for post exploitation tasks such as command execution and data extraction.
Hydra: A fast and flexible password-cracking tool designed to perform brute-force and dictionary-based attacks on various network protocols, including SSH, HTTP, FTP, and more.
SecLists: A comprehensive collection of penetration testing resources, including wordlists for usernames, passwords, web directories, and other payloads used in reconnaissance and exploitation phases.
NetExec: A network exploitation tool that enables remote command execution on target machines through various protocols, assisting in lateral movement and privilege escalation scenarios.
XFreeRDP: An open-source implementation of the Remote Desktop Protocol (RDP), enabling penetration testers to connect to and control Windows systems remotely for reconnaissance and post-exploitation purposes.
Guides Numerical Order¶
Below is the numerical order for the step-by-step guides. These guides serve as the basis for the project. It is recommended the respective guide docs page is opened while following along in the program.
👉 If you prefer to follow content by reading, these guides on this docs site will provide the same information as the video lectures.
Guides¶
-
Provisioning VMs
- VirtualBox
- VMware Workstation Pro
-
Servers
- AD Server - Provision & Setup Windows Server 2025
- Workstations
- Provision & Setup Windows 11
- Provision & Setup Ubuntu Desktop 22.04
- Servers
- Corporate Server - Provision & Setup Ubuntu Server 22.04
- Tool Guides
- Email Server - MailHog
- Workstations
- Provision & Setup Security Onion
- Servers
- Security Server - Provision & Setup Ubuntu Server 22.04
- Tool Guides
- SIEM - Setup Wazuh
- Configure a Vulnerable Environment
- Cyber Attack Simulation
Guides Format
The screenshots always conform to step in text, then screenshot evidence below it.

We hope you enjoy this section!
Made with ♥ by ProjectSecurity.io.